For Leaders: The AI Audit Closeout Template That Assigns Authority Fast
AA-001: The Audit That Changed Everything
Previous and Top of the Series:
Case Summary
Your last AI audit changed nothing.
The report was thorough. The risks were documented. The meeting happened. Then the system kept doing exactly what it was doing before, because nobody with real authority ever touched it.
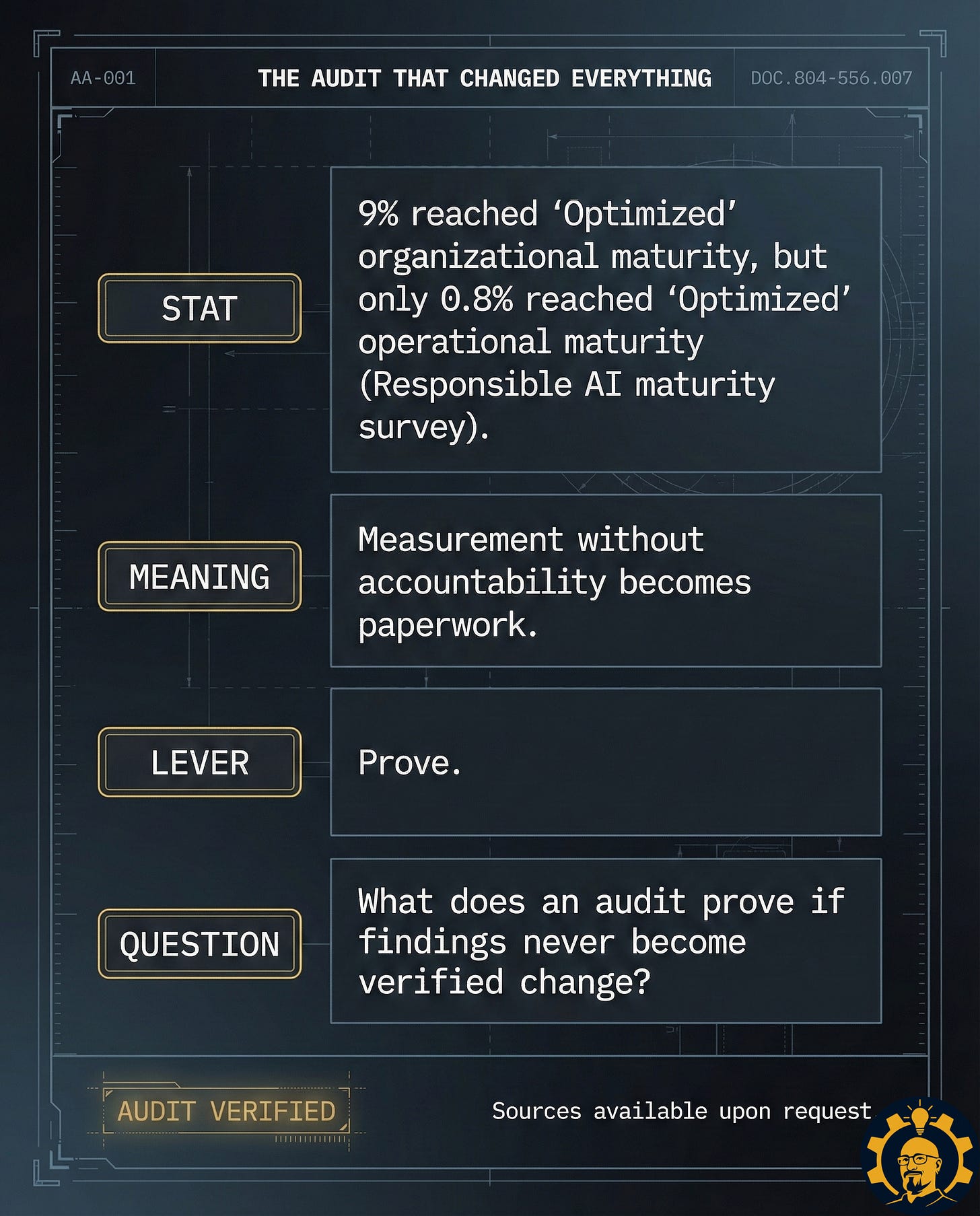
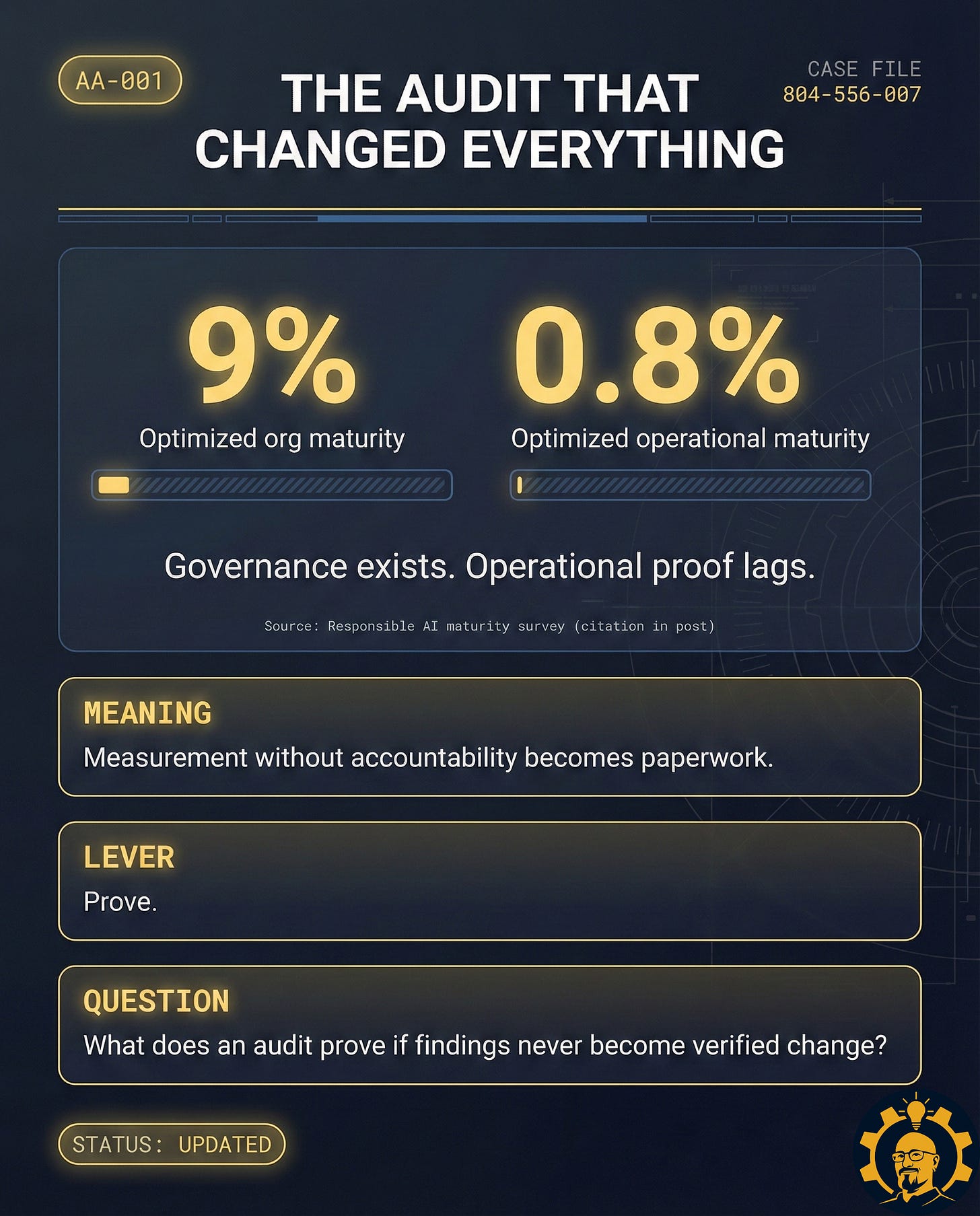
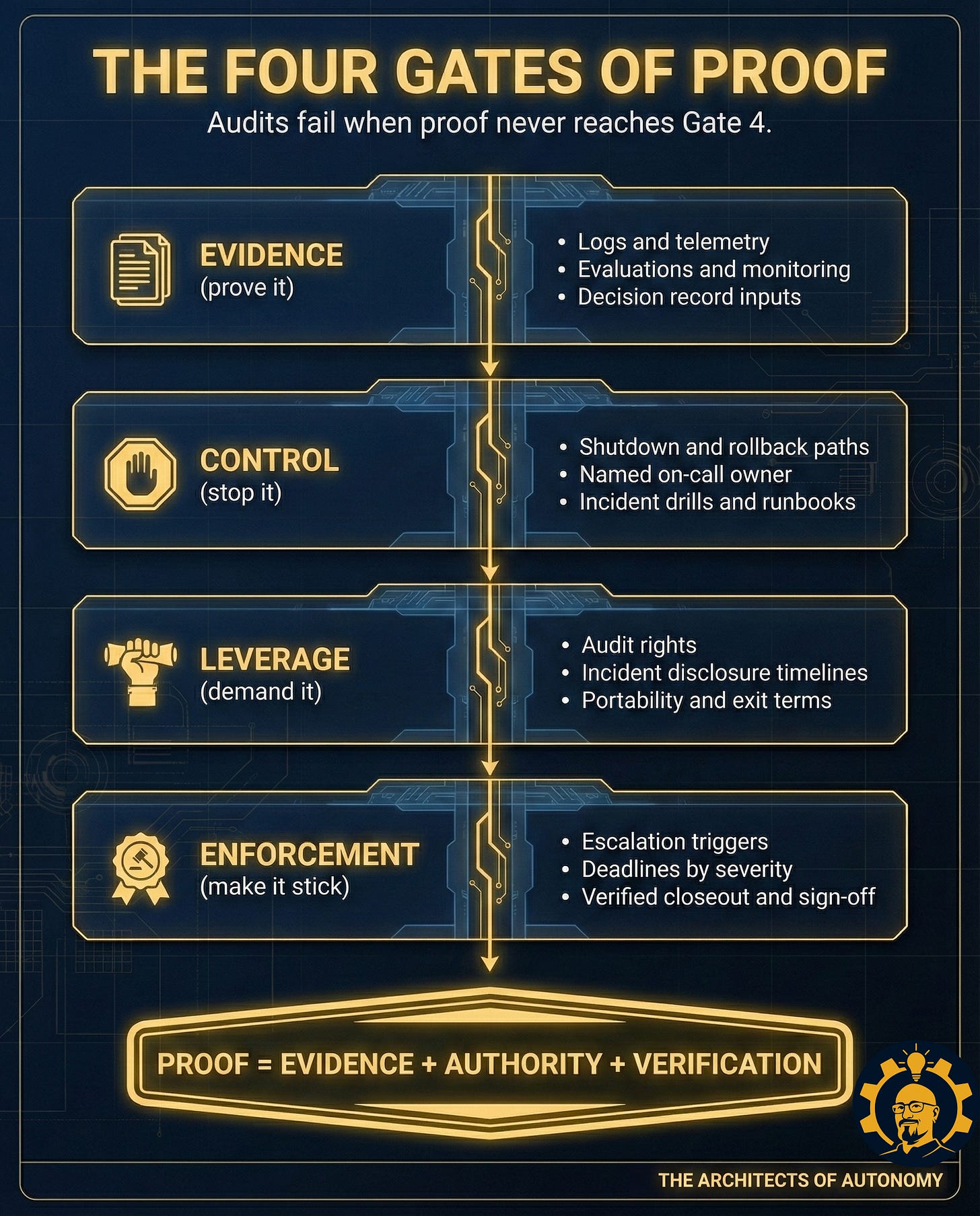
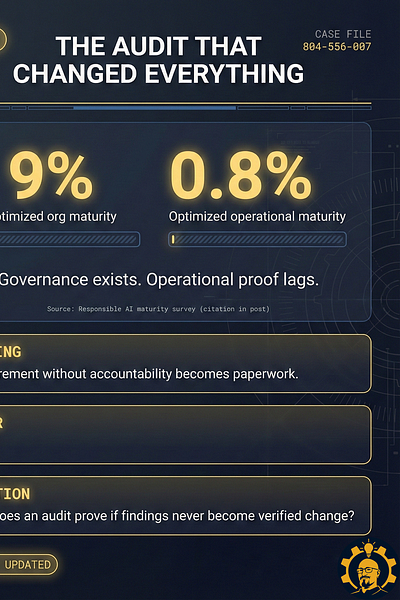
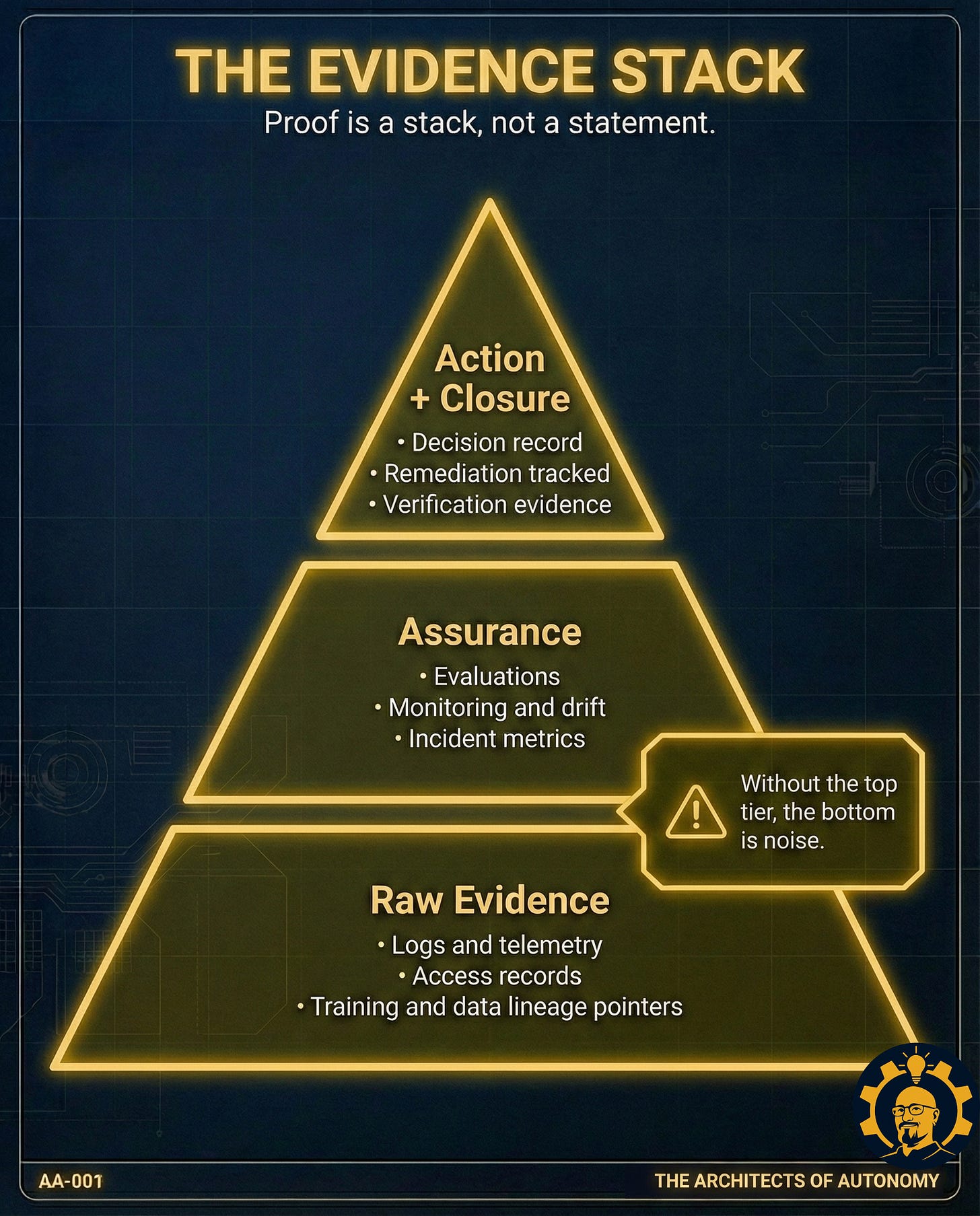
Here is the problem: a recorded finding is not proof. Proof is Evidence + Authority + Verification. Most AI audits have evidence. Almost none have authority. Without authority, you do not have governance. You have documentation of the moment you chose not to act.
This post gives you the one-page Audit-to-Authority Map that forces every finding to have a named owner, a real decision right, and closeout evidence you can re-audit. The rule is simple:
PANEL: AA-001 RULE
If fields 6–12 are blank, you do not have an audit. You have documentation.
Use this map on your next AI system review, vendor audit, or closeout meeting. If you cannot fill out all 12 fields, do not sign off.
Scene: The Map Room
You step into the Map Room.
The lights buzz. The report is polished. The spreadsheet is color-coded. The risks are “noted.”
You already know what comes next. Nothing.
Somewhere, a model keeps doing the thing you said mattered. Somewhere, a decision keeps getting made by default. Somewhere, a Slack thread is pretending to be governance.
The audit is complete. The harm is not.
A finding was recorded. No owner was named. No right to act was assigned. That is not proof. That is a receipt.
Proof is closure. Here is the template that makes closure mandatory.
Exhibit A: Receipt Audit vs Real Audit
Most AI audits look impressive in the same way a perfectly itemized receipt looks impressive.
It tells you what was purchased.
It does not tell you whether anything changed.
A receipt audit is what happens when measurement exists, governance exists, and outcomes keep drifting anyway. The checklist is completed. The risks are noted. The meeting happens. Everyone feels “responsible.” Then the system returns to its default settings, because nobody with a real decision right ever touched the controls.
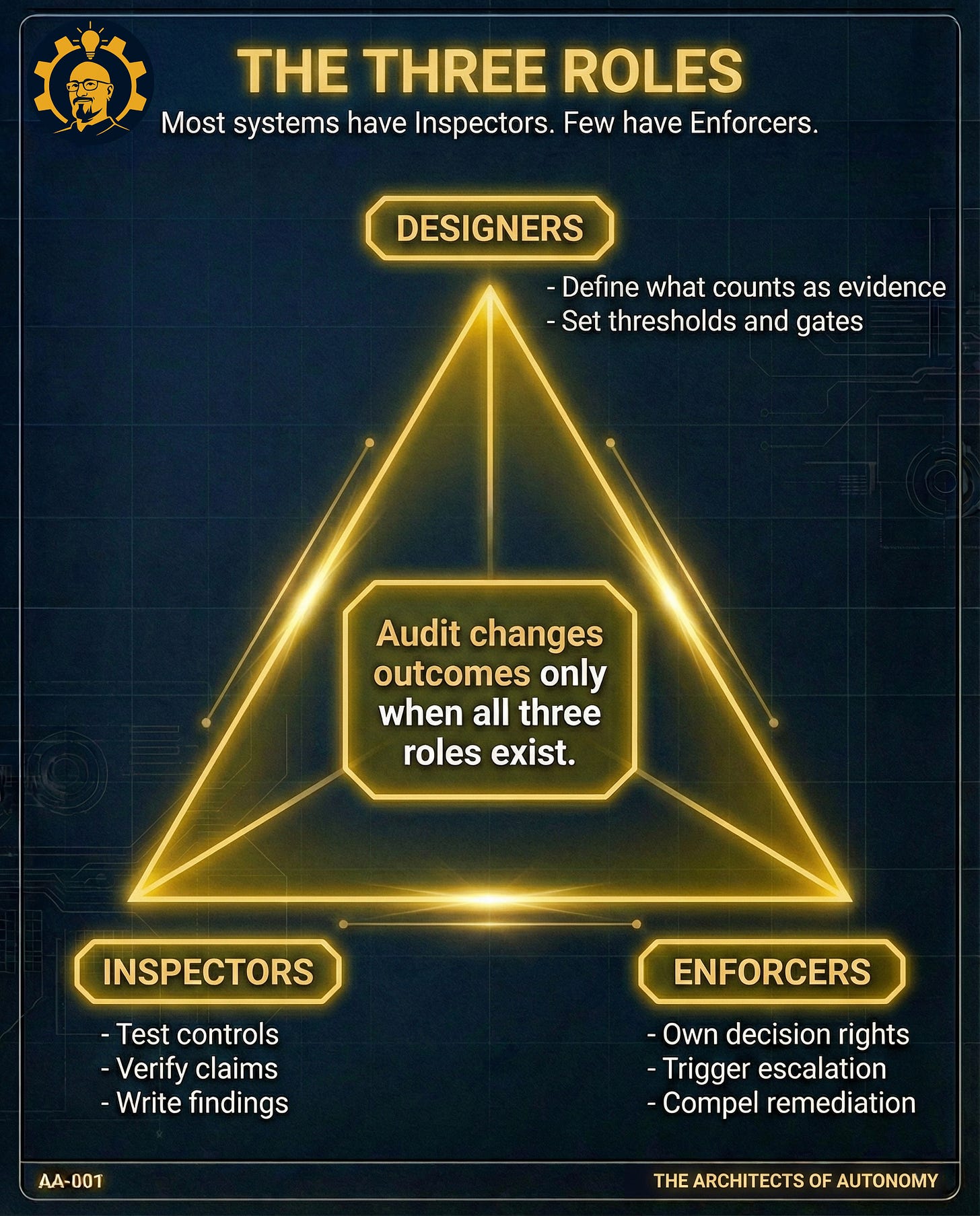
A real audit is not a report. It is an intervention. It links evidence to an owner, an owner to a decision right, a decision right to a deadline, and a deadline to verification.
▶ PANEL: SAME PAPERWORK. TWO REALITIES.
Receipt audit
Checklist completed
Risks noted
Owner: TBD
Deadline: TBD
Verification: none
Output: comfort
Real audit
Evidence linked to owner
Owner named (person, not team)
Decision right explicit
SLA assigned with consequences
Closeout verified (re-audit required)
Output: control
Here is the part nobody wants to say out loud:
If your audit cannot force a change, it is not protecting autonomy. It is documenting the moment you handed autonomy away.
▶ PANEL: AA-001 RULE
If fields 6–12 are blank, you do not have an audit. You have documentation.
Exhibit B: Proof Without Power (with concrete example, no made-up numbers)
Same system. Same audit. Same finding. Two endings.
The outcome of an audit is not determined by how accurate the finding is. The outcome is determined by whether the finding has power.
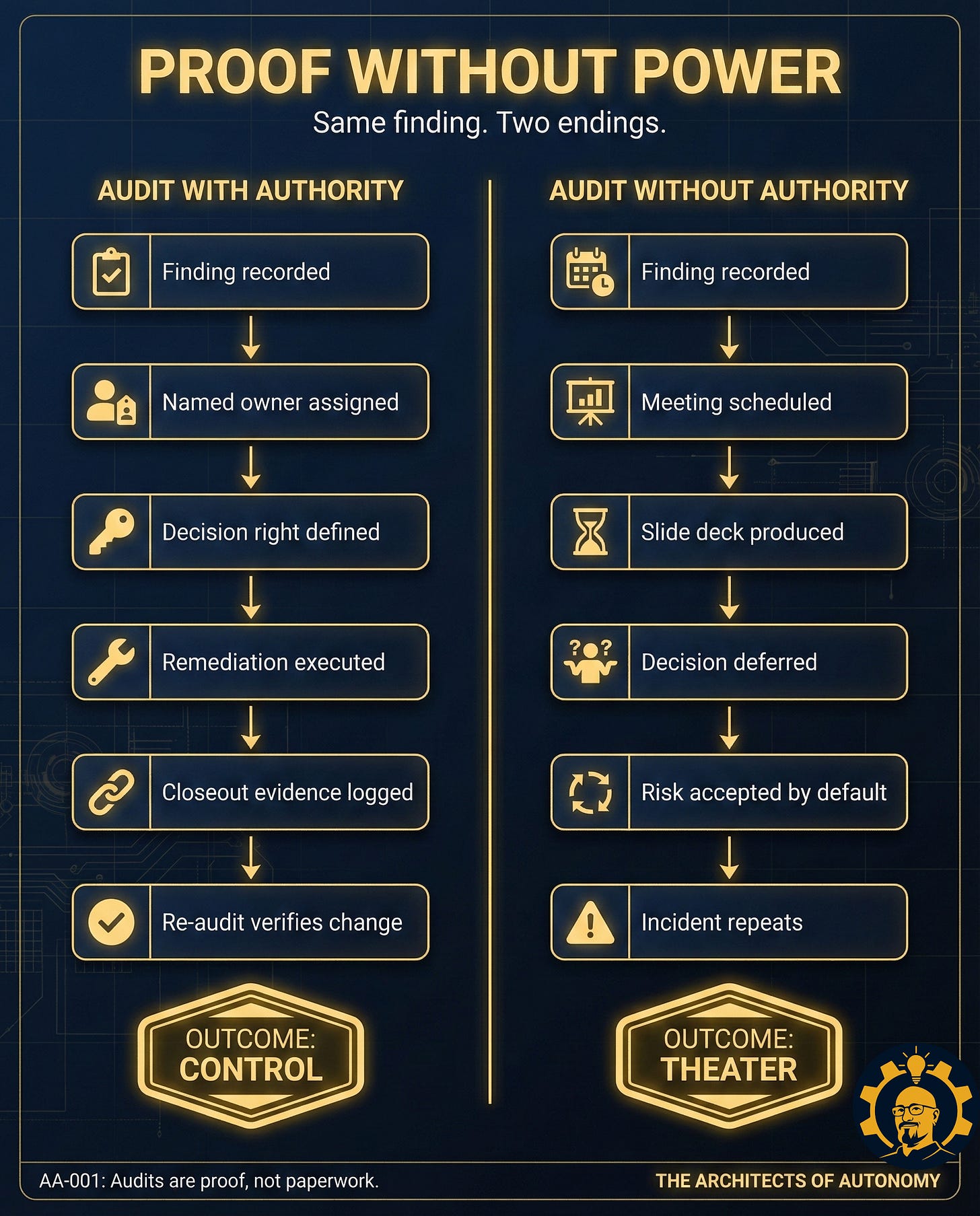
Ending One: Audit With Authority
The finding is recorded, but it does not stay in the report.
A named owner is assigned. Not a team. Not a committee. A person.
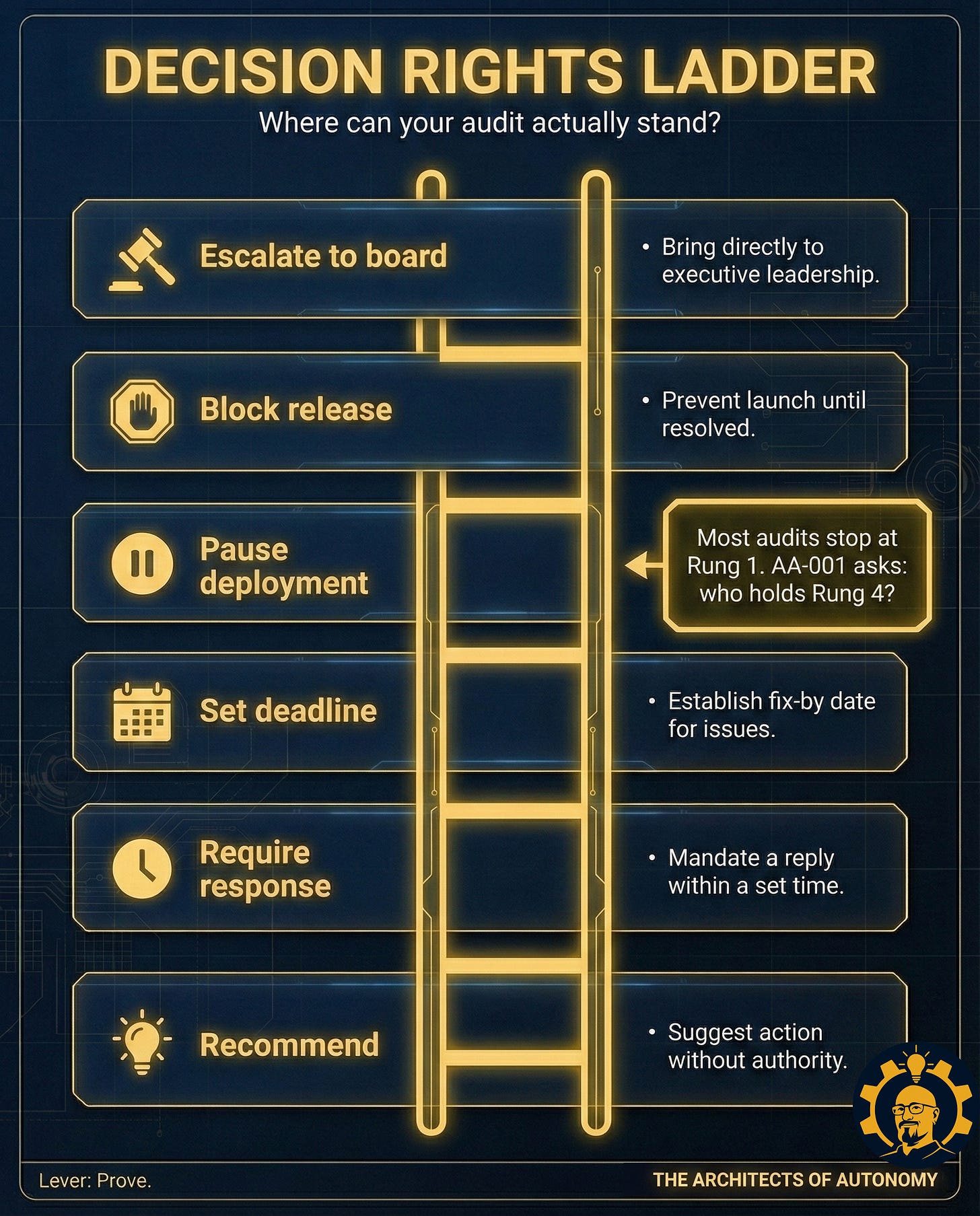
A decision right is defined. Not “recommend.” A real lever: pause deployment, block release, require human review, escalate beyond the team that built it.Remediation happens in daylight. A fix-by date exists. People feel the deadline.
Then the part most organizations skip:
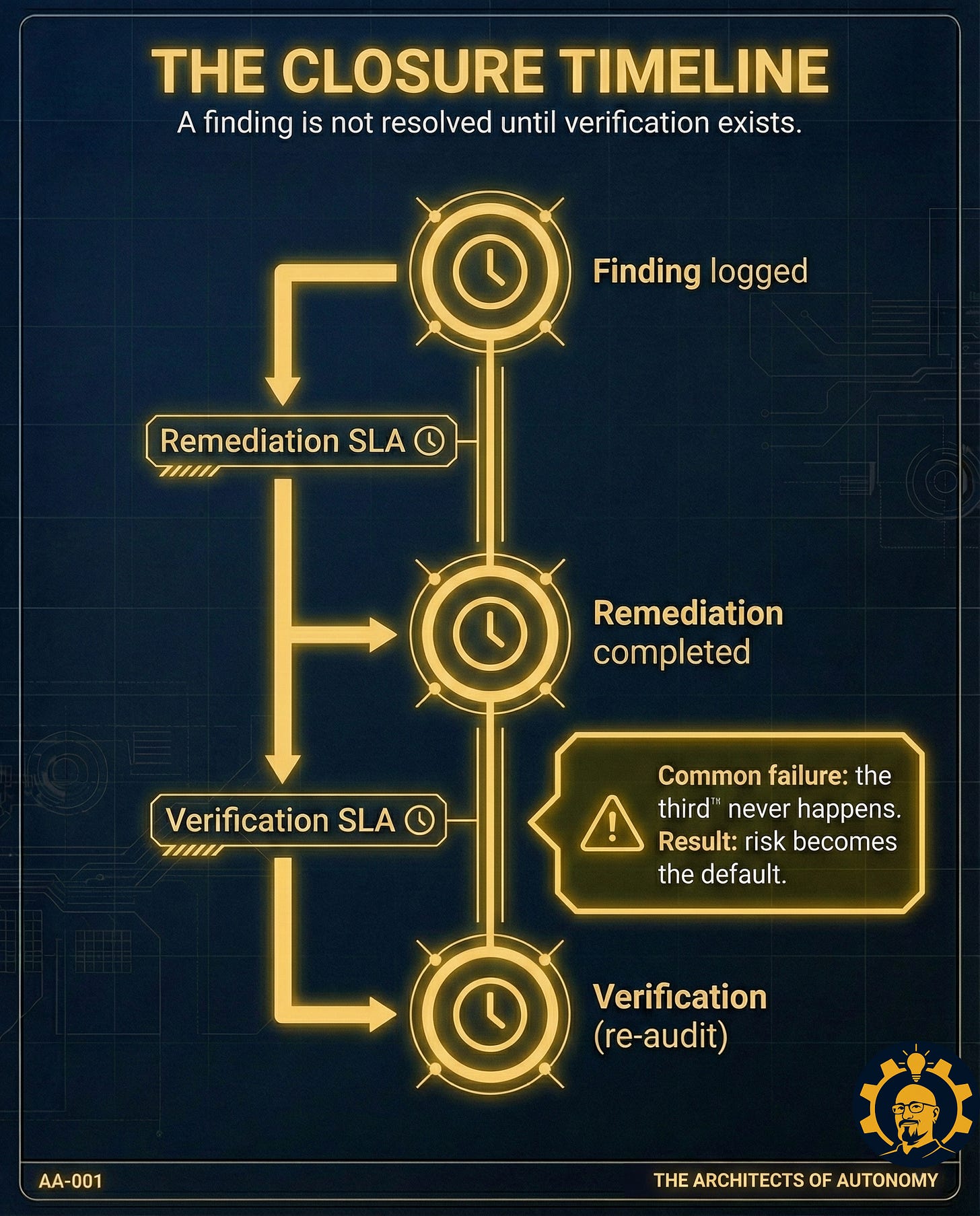
Verification.
A re-audit confirms the change. Closeout evidence is logged. The finding is not “resolved” because someone said it was. It is resolved because proof exists.
That is what control looks like. It is not dramatic. It is boring. It works.
Ending Two: Audit Without Authority
The finding is recorded. The system becomes polite.
A meeting is scheduled. A deck is produced. The decision is deferred.
Someone says, “We will revisit next quarter.” Someone else says, “We need more data.” Ownership stays fuzzy, because fuzziness is a survival strategy in organizations that punish accountability.
Eventually, the risk is accepted by default. Not by signature. Not by governance. By gravity.
The incident repeats.
Curious About My Specific Sources? See Attached Detailed PDF Below:
Supplemental Spreadsheet for Enterprise Proxy Statistics: Measurement Outpacing Governance:
Concrete Example: The Moderation Audit That Changed Nothing
A company audits its AI-powered content moderation system. The finding: the model flags legitimate educational content as harmful above the agreed threshold, blocking teachers and researchers.
Receipt audit path:
Risk documented. Severity: High. Owner: “Product and Trust & Safety teams.” Remediation: “Explore tuning and threshold adjustments.” Deadline: “Pending roadmap prioritization.”
Result: weeks later, support tickets keep coming. The system keeps doing the same thing. Nobody had the right to stop it, so nobody did.
Real audit path:
Risk documented. Severity: High.
Owner: a named executive for Trust & Safety. Decision right: require human review for specified categories, pause automated bans, escalate if SLA is missed.
Deadline: mitigation by SLA, full fix by SLA.
Verification: re-audit confirms the agreed metric improves and holds for two reporting cycles.
Result: the audit stops being a report. It becomes a control surface.
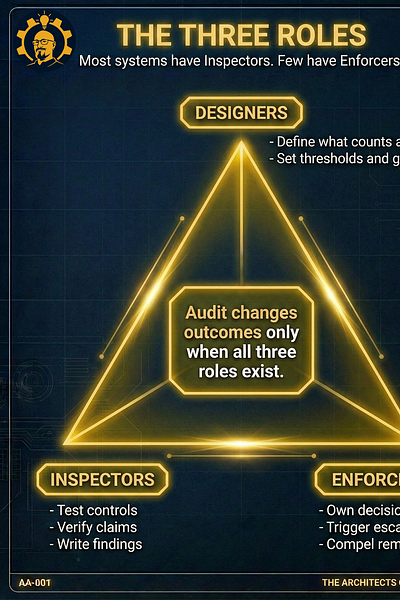
The Test: Who Can Actually Act? (panel)
A finding without authority does not become action.
It becomes a story people tell themselves about being careful.
▶ PANEL: FOUR QUESTIONS THAT EXPOSE THEATER
Does someone have the right to pause the system?
Does someone have the right to block release?
Does someone have the right to escalate beyond the team that built it?
Does verification exist after remediation?
If the answer is no, the audit proved you can measure risk.
It did not prove you can govern it.
Proof is not a report. Proof is closure.
You can believe every word of this post and still walk out of the Map Room with nothing changed.
So here is the artifact. The one-page closeout map that turns findings into levers, and levers into verified outcomes.
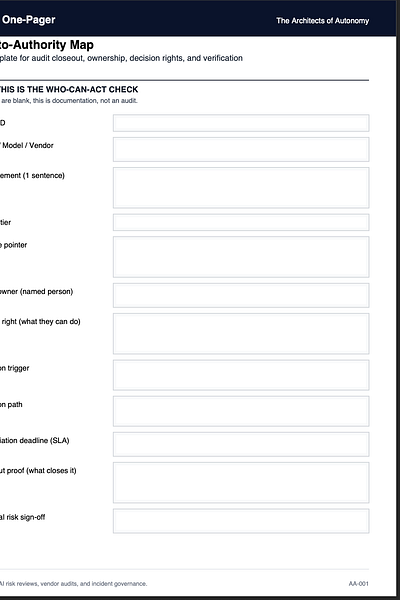
Case File Insert: Audit-to-Authority Map (Illustrative Example)
▶ PANEL: THIS IS THE WHO-CAN-ACT CHECK
If fields 6–12 are blank, this is documentation, not an audit.
Finding ID: AA-001-F-014
System / Model / Vendor: Customer Support Triage LLM, Vendor X
Risk statement (1 sentence): Model escalates false “policy violations,” causing wrongful account restrictions for legitimate users.
Severity tier (Low/Med/High/Critical): High
Evidence pointer (logs/evals/tickets): Incident tickets #2418–#2431, audit log set “TRIAGE-Q2,” eval run “toxicity v3,” screenshot packet in case file
Control owner (named): Director of Trust and Safety Operations (name in internal doc)
Decision right (what they can do): Pause automated restrictions, require human review, approve rollback to previous prompt chain
Escalation trigger: 3+ wrongful restrictions in 24 hours OR any protected-class proxy flagged in review set
Escalation path: On-call T&S lead → VP Product → Risk Committee notification within 24 hours
Remediation deadline (SLA): 10 business days for mitigation, 20 business days for full fix
Closeout proof (what closes it): Re-audit shows false restriction rate below threshold for two consecutive weeks; rollback capability tested in drill; decision record updated
Residual risk sign-off: VP Product + Legal Counsel sign-off recorded with rationale and review date
QA note: This is intentionally written so you can swap in your organization’s specific thresholds, windows, and SLA numbers without inventing anything.
Stop “Audit Theater”! Download the 1-Page AI Audit Closeout Map and Assign Authority in Minutes:
How to Use This in a Meeting (30-second script)
PANEL: CLOSEOUT SCRIPT (READ THIS OUT LOUD)
“Before we close this finding, we are doing the authority check.
Field 6. Who owns this, name a person.
Field 7. What can they do, name the lever. Pause, block, rollback, or escalate.
Field 10. What is the deadline, and what happens if we miss it.
Field 11. What evidence closes this, and who verifies it.If we cannot fill fields 6 through 12 in this room, we do not have an audit. We have a status update. We are not closing the finding.”
“Blank fields are blockers. Not homework.”
Action Pack (Checklist Card Style)
PANEL: THE 30-MINUTE CLOSEOUT DRILL
Do this once and you will immediately see whether your audit program produces control or paperwork.
Step 1. Pull one audit.
Choose the last AI audit or risk review. Take the top three findings.
Step 2. Run the authority check (3 lines per finding).
Write: Owner (name), Decision right (lever), Closeout proof (verification).
If any line is blank, the finding is still open.
Step 3. Run the theater test (4 questions).
Pause, Block, Escalate, Verify.
Any “no” is theater.
Step 4. Fill one full map.
Pick the most consequential finding. Fill all 12 fields. Do not polish. Discover where governance breaks.
Step 5. Schedule the authority check meeting (15 minutes).
Invite the control owner plus one leader who can grant decision rights. Agenda is fields 6–12 only.
PANEL: LEADER MOVES (DO THIS THIS WEEK)
These are small policy moves that change outcomes immediately.
1) Standardize the 12-field rule.
No AI finding closes without a completed Audit-to-Authority Map.
2) Reopen one “closed” finding and demand proof.
Ask for the verification artifact. If it does not exist, reopen the finding and assign decision rights.
3) Make authority gaps escalate.
If a finding cannot be assigned a named owner with decision rights within a defined window, it escalates to you.
PANEL: REMINDER
A finding is not resolved when remediation is “done.”A finding is resolved when verification exists.
Transition out of the Action Pack
This is what makes an audit real. Not the report, not the meeting, not the deck.
A named owner. A decision right. A deadline. A verification step.
Proof is closure.






Sharp reminder that AI audits only matter when findings come with clear ownership, decision rights, and verified closeout, not just documentation
Your infographics are really cool!🩷🦩