8 Breakpoints, 10 Controls, 60 Minutes, $561M Saved
🔒 Leader's Dispatch: Volume 30 (Click to Catastrophe, Part 1 of 7 Part Series)
Previous:
Click to Catastrophe, Episode 1: Pig Butchering
How it works. How it spreads. How to shut it down.
And the most dangerous moment is not the first message.
It is the moment you feel embarrassed.
Not because embarrassment makes you weak. Because embarrassment makes smart people go quiet, go fast, and go solo.
I have watched this dynamic play out in rooms full of high performers for two decades. On improv stages. In government programs. In enterprise transformations where one “tiny” decision can turn into a seven-figure fire drill.
The system wants you isolated. It wants you improvising alone.
And if you are thinking, “I would never fall for something like this,” congratulations. That is also a system response.
A quick primer before we go any further
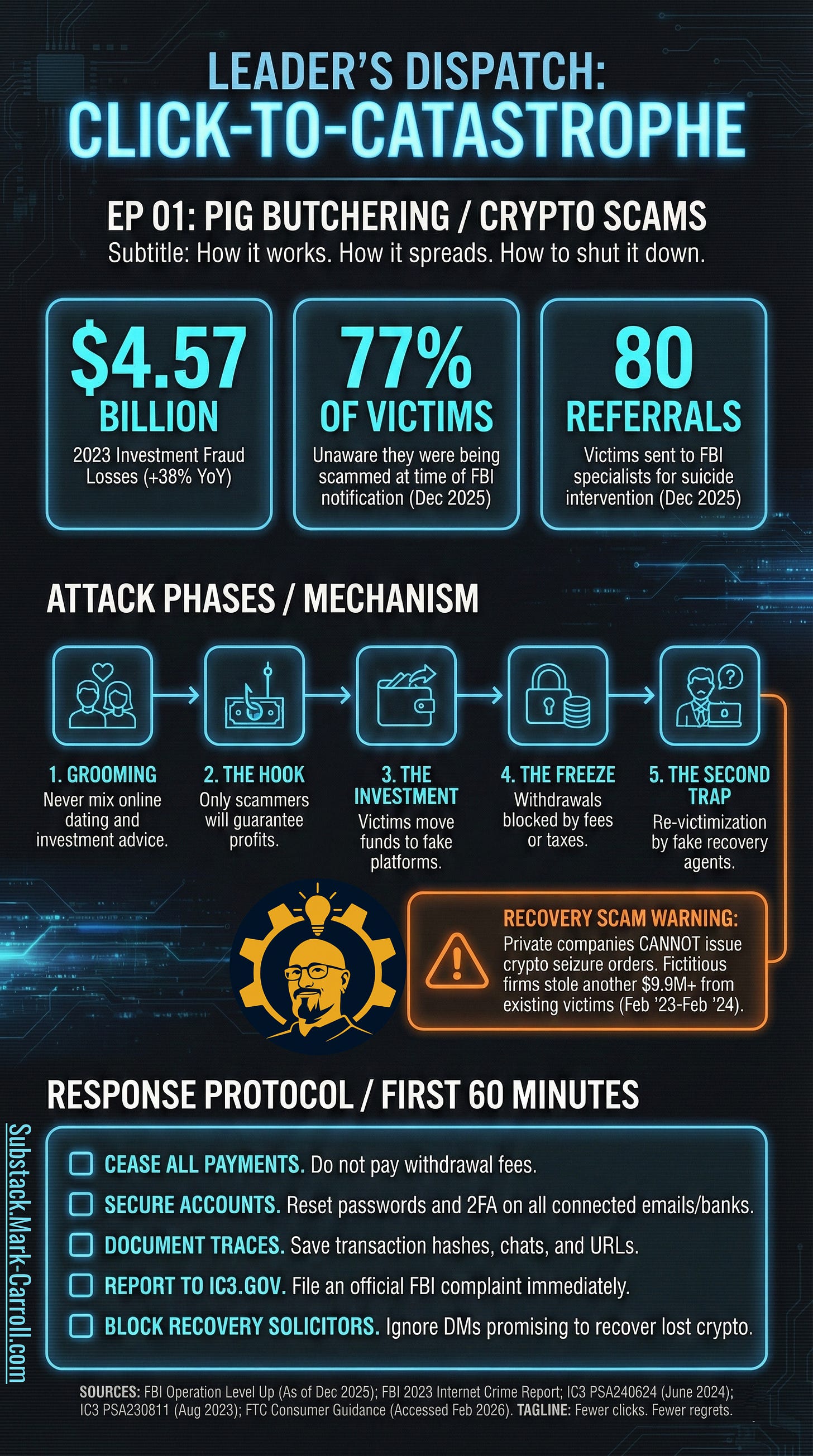
This episode is about a scam type called pig butchering.
Calling it “pig butchering” sounds alarming, and it often is. Either way, we still need to learn the pattern.
Why the name: the scam is structured like a long con where the victim is “fattened” with attention, trust, and small wins before the extraction. The point is not the word. The point is the sequence.
And here is the key move that makes pig butchering different from a basic “send me money” scam:
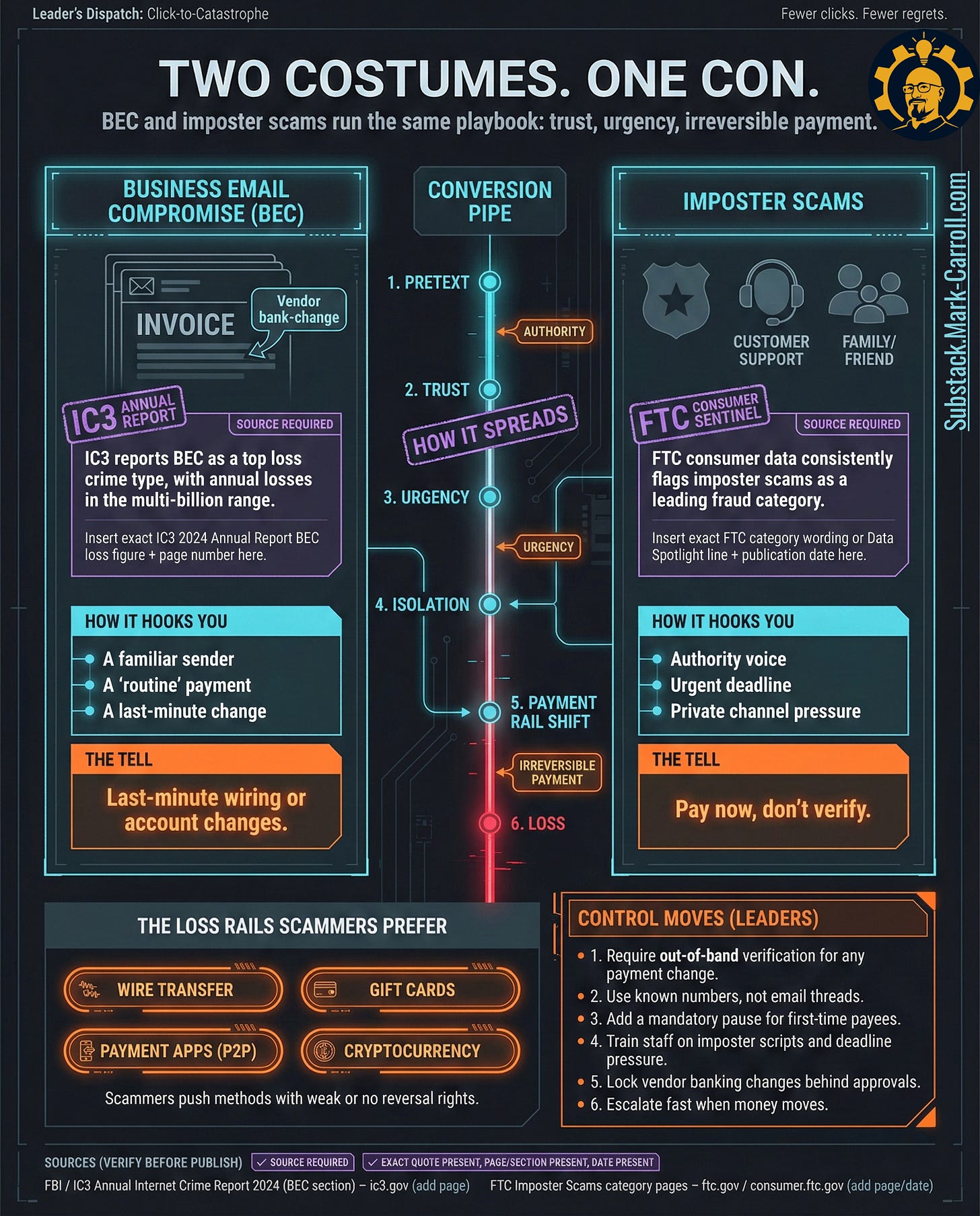
It feels like relationship first. Then opportunity. Then urgency. Then shame.
That sequence is what we are going to break.
One extra credibility line, because this matters: in compliance-heavy environments, you learn quickly that “verification” is not bureaucracy. It is how you keep a bad day from becoming a permanent one.
Now let’s map the pattern.
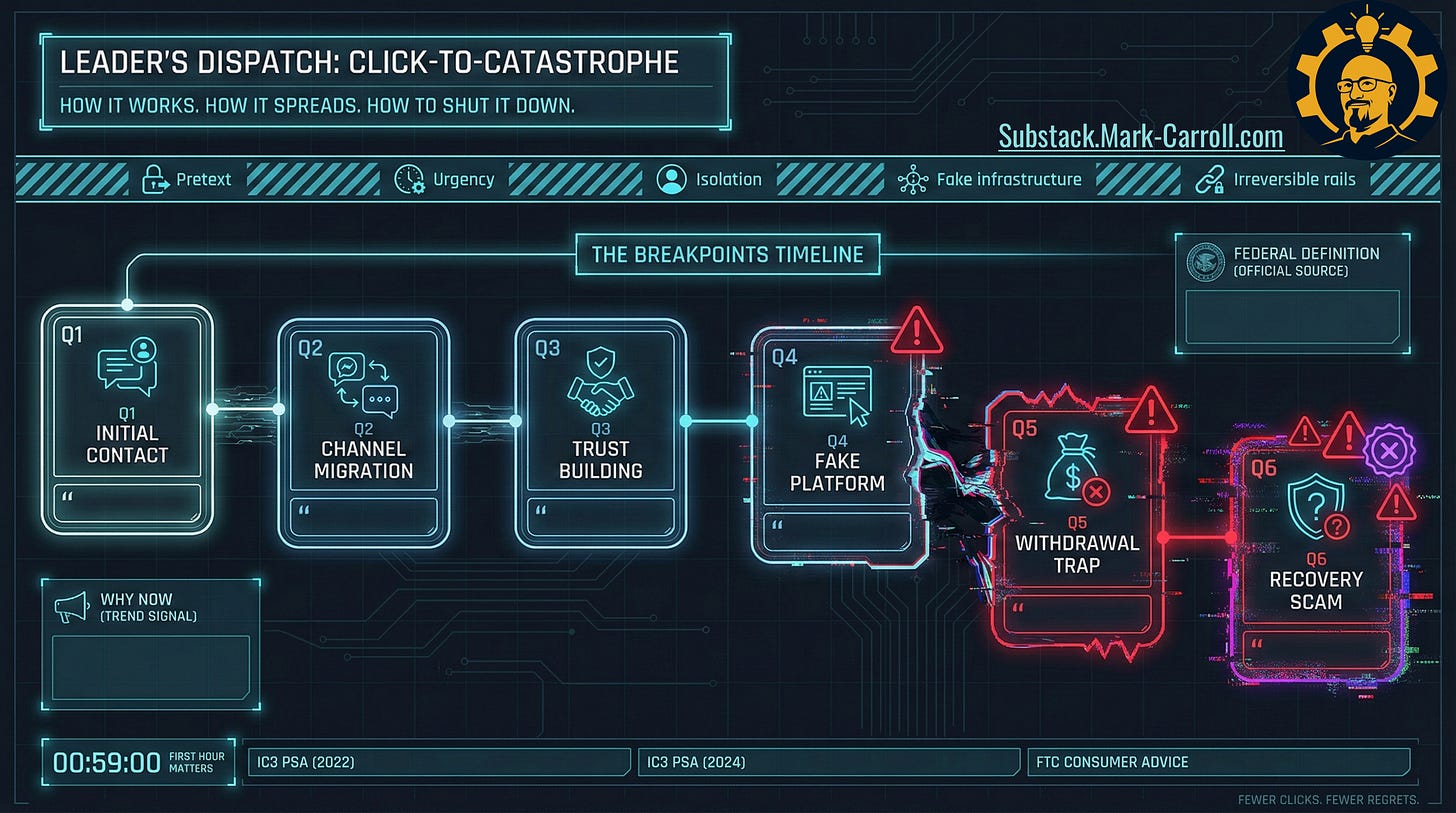
The breakpoint framework (B1 to B8)
In the ensemble, every member carries a piece of reality.
Scams try to remove the ensemble.
They do it with a series of breakpoints, each one nudging you toward private decision-making.
Below is the arc. You do not need to memorize it. You just need to recognize where you are so you can stop climbing the ladder.
B1: The “normal” opener
A message that looks harmless.
Often friendly.
Often mundane.
This is not a hack of your bank account. It is a hack of your social reflexes.
In improv, you accept offers because you are building something together. In scams, they are using that same human instinct to get you to accept a premise without checking the stage you are standing on.
Early defense:
Do not reward unknown openers with momentum.
Slow the tempo. Ask one grounding question.
Move the conversation back to a verified channel if it matters.
B2: Consistency and cadence
They show up again.
Same tone.
Same responsiveness.
Same drip of attention.
The system wants you to confuse consistency with legitimacy.
This is also where people start thinking: “They are so consistent, it would be rude to question them.”
That is a collaboration instinct.
It is also a vulnerability.
B3: Personal disclosure that invites reciprocation
They share something small, then slightly larger.
A little vulnerability.
A little struggle.
A little intimacy.
Not because they want closeness. Because closeness makes scrutiny feel like betrayal.
In the ensemble, trust grows through shared risk. Here, the risk is one-directional.
B4: The “world expands”
They introduce a broader narrative:
a friend who made money
a method
a platform
a “mentor”
an inside track
This is the moment the conversation stops being social and starts becoming a system.
And systems have controls.
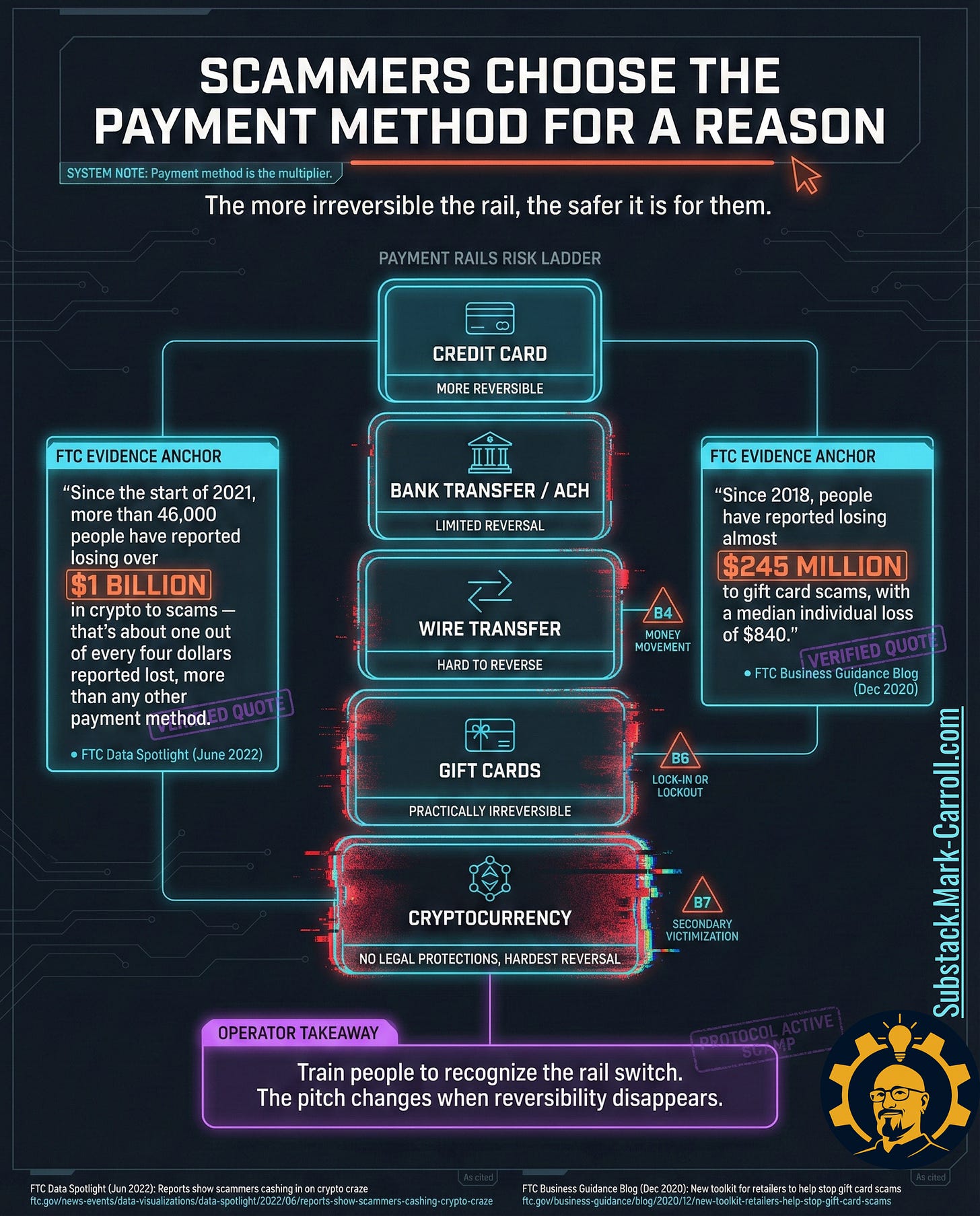
Which is exactly why the scam wants you off your controls.
B5: The first small “win”
A tiny test.
A small deposit.
A small return.
A feeling of, “Huh. That worked.”
This is where your brain starts trying to protect the story.
Because the story feels good.
B6: Channel migration
This one is so common it deserves its own alarm.
They want you to move off the platform where you found them.
To a private messenger.
To a new number.
To a new app.
To a new email.
Not because it is more convenient.
Because once you migrate channels, you also migrate accountability.
A simple rule that saves people:
Any financial conversation that leaves your verified channel triggers out-of-band verification. Period.
Not because you are paranoid. Because you are sane.